Recently Azure has switched off the old portal and along with it the old Azure AD client. In the old portal there was a way to invite guests and members. In the new portal you can currently only invite guests, if you would like to invite members you need to do this through PowerShell. In this blog post we are going to take a look at how B2B actually works and how you can invite members.
What is a difference between a member and a guest user type? User type is used to enforce different security polices, Microsoft has written some great documentation about this. I found this image extremely helpful in their documentation:
How B2B invite works
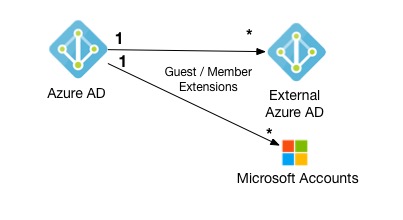
Let's unpack what is happening in the image above. You can invite users from external Azure ADs and Microsoft Accounts. You can't invite users from Google Identity, etc. The whole B2B collaboration feature works in Microsoft ecosystem only. This means if your company decides to invite 3rd party company users that does not have Azure AD then these users will end up creating Microsoft Accounts to login in to your service.
How to invite members from external Azure AD
Let's say that Elliot Alderson works for ECorp, his original account is residing in ecrophq.onmicrosoft.com Azure AD. Elliot Alderson works for Ecorp Fraud department. ECorp fraud department has decided to get their own Azure AD as they want to enforce their own security rules on their subset of users. Also, they do not want to call ECorp HQ IT department every time they want to setup a brand-new application for authentication (client id, audience, etc).
In this case ECorp Fraud admin will need to run the following script. To keep things simple when this admin calls Connect-AzureAD he will just use adprincipal@ecorpfraud.onmicrosoft.com account to authenticate and invite Elliot.
Connect-AzureAD New-AzureADMSInvitation -InvitedUserEmailAddress "elliot.alderson@ecorphq.onmicrosoft.com" -InviteRedirectUrl https://www.ecorp.com -SendInvitationMessage $true -InvitedUserType Member
Once Elliot receives the email and accepts invitation this is how this setup will look like:
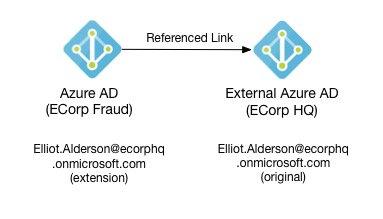
I do not know about the Azure AD internals, so I am going to speculate now. It seems that when you add a user from external Azure AD in to your Azure AD it creates this user record as an extension. When Elliot gets the invite or is given the consent URL and approves permissions, referenced link gets created so Azure AD knows where to redirect user to authenticate.
No comments:
Post a Comment